KBI 310908 New Feature: Monitor Windows Network Share
Version
Added to Argent for Compliance 3.1A-1401-T5 and later
Date
Wednesday, 9 Apr 2014
Summary
Argent for Compliance 3.1A-1401-T5 and later allow customer to monitor various activities and settings of Windows Network Share
It also provides reports that list existing shares as well as changes
Technical Background
Argent for Compliance uses WMI to retrieve Network Share information
As a result, Argent AT engine must have WMI access to the target machine in order to do the monitoring
Argent for Compliance compares the newly retrieved Network Share Information with cached result to figure out what are changed since last check
But this does not generate the information of who made the change
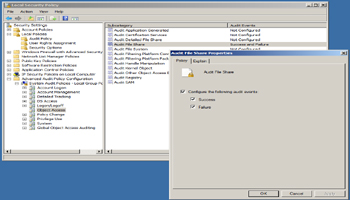
For Windows 2008 and later, it is possible by turning on the Audit File Share to get the information
Because of the resulting Audit Event volume especially on file server and Domain Controller can be significant, customer should consider the trade-off if he truly needs the information
Customer needs first turn on the file share audit under Advanced Audit Policy Configuration
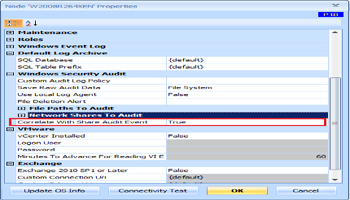
Customer then need to tell Argent for Compliance engine to query Audit Event to get the ‘Who‘ information
Argent for Compliance 3.1A-1401-T5 introduces following new Rule types to monitor Windows Network Share:
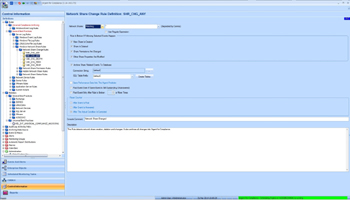
- Network Share Change Rule – It monitors share creation, deletion, property changes and permission changes
It can optionally save changes to archive database, which is required for reporting
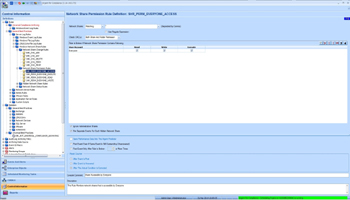
- Network Share Permission Rule – It Alerts on shares that have unwanted permissions
For example, it is very bad if share permission is not configured or share is open the access to EVERYONE
Network Share Access is actually controlled by both permission for the share and permission for the share folder
A hacker must pass the test of both permission tests in order to access the share
Unfortunately, a carelessly created share may have both wide open for EVERYONE access
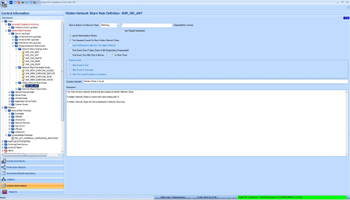
- Hidden Network Share Rule – It detects the hidden shares
A hidden share is a share with name trailing with ‘$‘
A hidden share won’t show up in Network Browsing
It can be a trick for hacker to create a hidden access to the server
Also, Windows machine has Administrative Shares such as ADMIN$, C$, D$ etc turned on by default
They can be hacking targets too
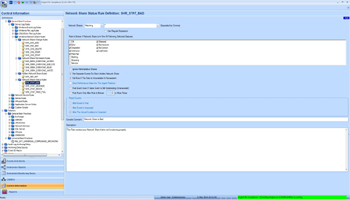
- Network Share Status Rule – It monitors Windows Share Status
The most important statuses to watch out include Error, Degraded and Pred Fail (Predicative Failure)
The Rule can be very useful if the share is built on cluster
It allows customer to catch the partial failure before the whole share is broken down
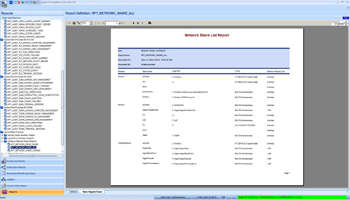
- RPT_NETWORK_SHARE_ALL – List all discovered Windows Network Shares
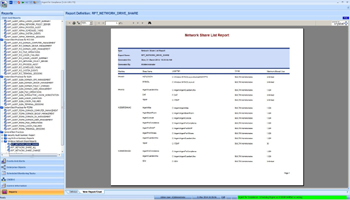
- RPT_NETWORK_SHARE_DRIVE – List all discovered Windows Drive Shares
- RPT_NETWORK_SHARE_CHANGE – List all share changes in the specified time range and selected computers
Argent for Compliance has built-in reports for Windows Network Shares
Resolution
Upgrade to Argent Advanced Technology 3.1A-1401-T5 or later