KBI 311665 Issue Addressed: Failed To Connect To LINUX/Unix Server Using SSH After Hardening Windows Server
Version
Argent Advanced Technology 5.1A-1804-A and below
Date
Monday, 28 May 2018
Summary
Based on most recent Microsoft recommendations, following ciphers are regarded unsafe:
(TLS 1.0)
TLS_DHE_RSA_WITH_AES_128_CBC_SHA
TLS_DHE_RSA_WITH_AES_256_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA
(TLS 1.0)
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA
(TLS 1.1)
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA
(TLS 1.2)
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA256
TLS_RSA_WITH_AES_128_GCM_SHA256
TLS_RSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA256
TLS_RSA_WITH_AES_256_GCM_SHA384
Also SSL/TLS cipher suites use Diffie-Hellman a prime modulus smaller than 2048 bits:
(TLS 1.0)
TLS_DHE_RSA_WITH_AES_256_CBC_SHA with a Diffie-Hellman prime modulus of 1024 bits
TLS_DHE_RSA_WITH_AES_128_CBC_SHA with a Diffie-Hellman prime modulus of 1024 bits
(TLS 1.1)
TLS_DHE_RSA_WITH_AES_256_CBC_SHA with a Diffie-Hellman prime modulus of 1024 bits
TLS_DHE_RSA_WITH_AES_128_CBC_SHA with a Diffie-Hellman prime modulus of 1024 bits
Windows server could be hardened by disabling some ciphers. For example, 3DES can be disabled by applying following registry setting
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168]” Enabled”=dword:00000000
However, after Windows server used as Argent AT Engine is hardened, Argent AT Engine can fail to connect to some LINUX/Unix servers
The issue has been addressed in Argent AT 5.1A-1807-A
Technical Background
Argent AT Engine uses built-in SSH library by default to communicate with LINUX/Unix server
Argent AT Engine has to negotiate with LINUX/Unix server to pick encryption cipher that supported by both sides
By default, Argent AT Engine sends out “aes256-cbc,3des-cbc,aes256-ctr” as supported encryption algorithms
As Argent AT Engine does not know what ciphers are disabled by Windows, both sides might end up with an encryption algorithm that is disabled by OS
As a result, the SSH connection fails
Argent AT 5.1A-1807-A is enhanced to allow showing the negotiation detail when connection fails
To see the detail, do connectivity testing in License Manager
For example, a test result might be like following:
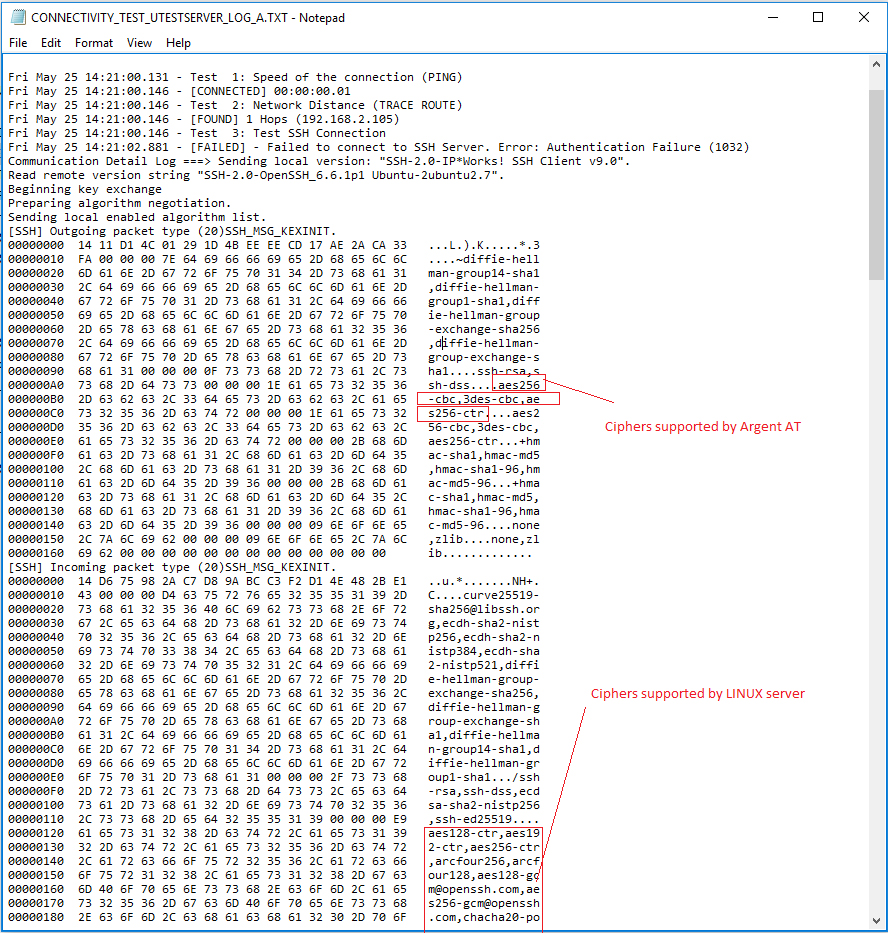
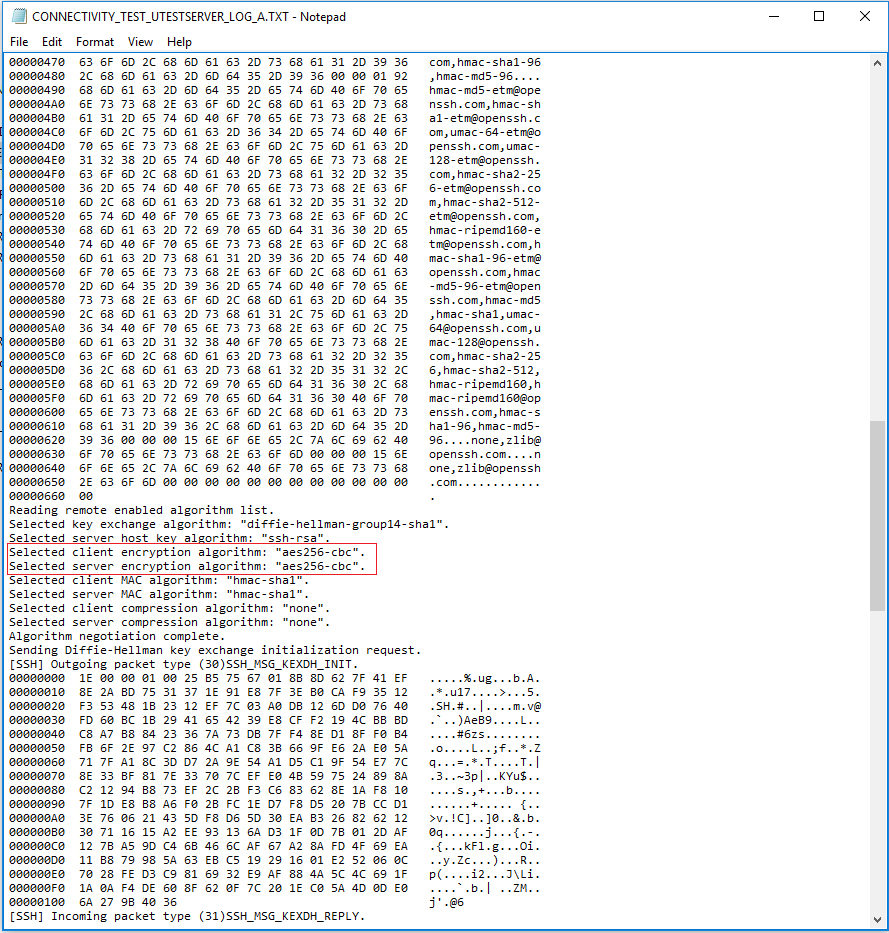
The log shows clearly what algorithm is selected
So it will be obvious what algorithm should not be used when connection fails
To specify the custom encryption algorithm, edit registry HKLM\Software\Argent\COMMON\ SSH_SUPPORTED_ENCRYPTION_ALGORITHM
It can take any combinations following text value:
aes256-ctr,aes192-ctr,aes128-ctr,aes256-cbc,aes192-cbc,aes128-cbc,3des-ctr,3des-cbc,blowfish-cbc,arcfour256,arcfour128,arcfour,cast128-cbc,aes256-gcm@openssh.com,aes128-gcm@openssh.com
It will take try and error to figure out what are the supported ones
For example, the previous test result shows ‘aes256-cbc’ is selected and not working, take it out of the string
Change registry, restart GUI and test again
The working combination can be found quickly
Resolution
Upgrade to Argent AT 5.1A-1807-A or above
For customer who cannot upgrade immediately, he needs to rollback using PLINK instead of built-in SSH library
To do so, change registry value to 1 for registry
HKLM\Software\Argent\COMMON\SSH_LIBRARY