KBI 312173 Using Read-Only Account In Argent Reporter To Prevent Bad Custom SQL Query From Damaging Database
Version
Argent Omega 2.2A-2404-A and later
Date
Thursday, 13 June 2024
Summary
SQL Query reports are versatile and extremely flexible to report any SQL data
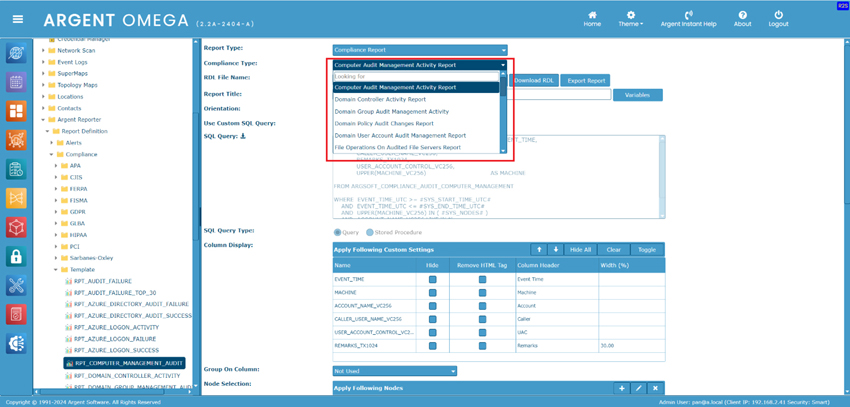
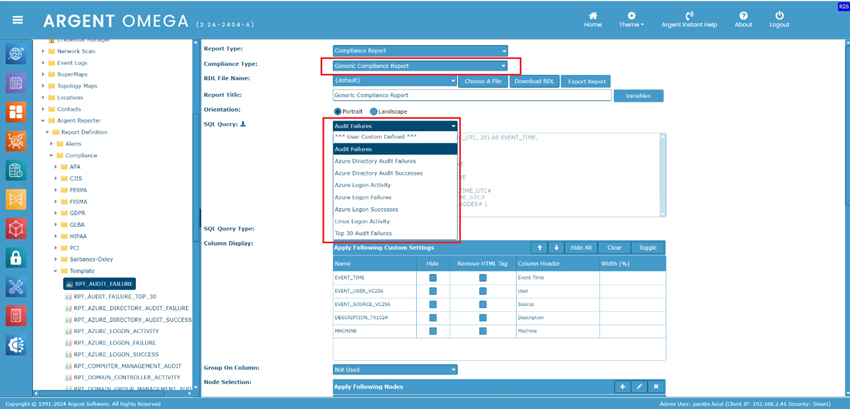
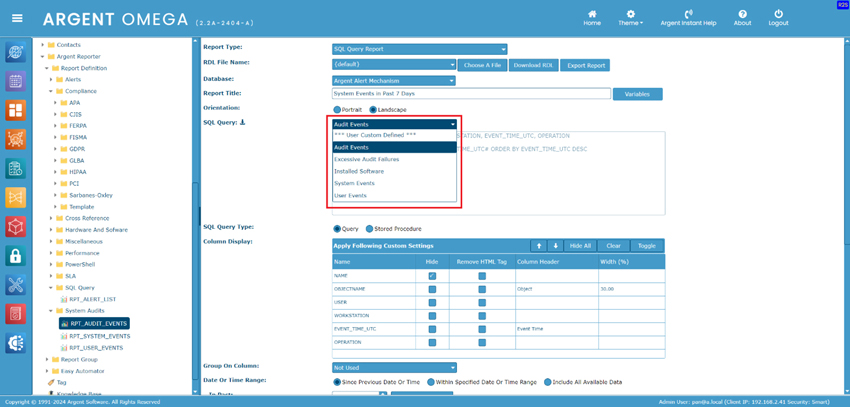
Argent Reporter provides built-in SQL queries for both Compliance Reports and SQL Query Reports.
Compliance Reports
Generic Compliance Reports
SQL Query Reports
Sometimes users may need to further customize the SQL query or create their own SQL query for reports.
Badly formatted SQL query might damage database. For example, a stored procedure might have syntax of deleting rows
The easiest way to avoid the unexpected consequences is to use the built-in SQL queries.
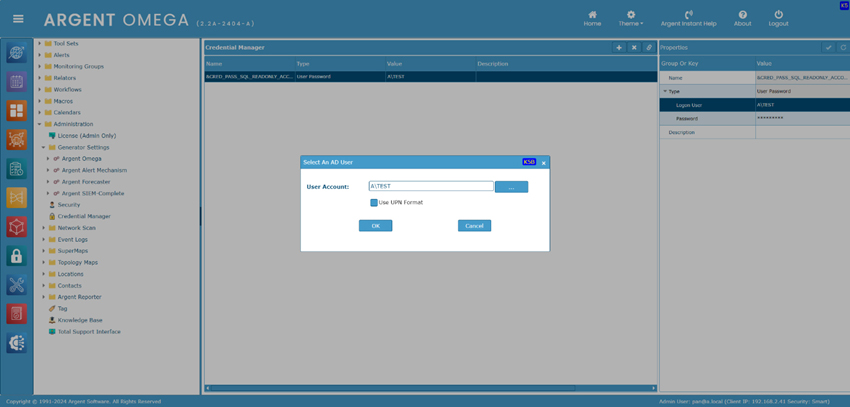
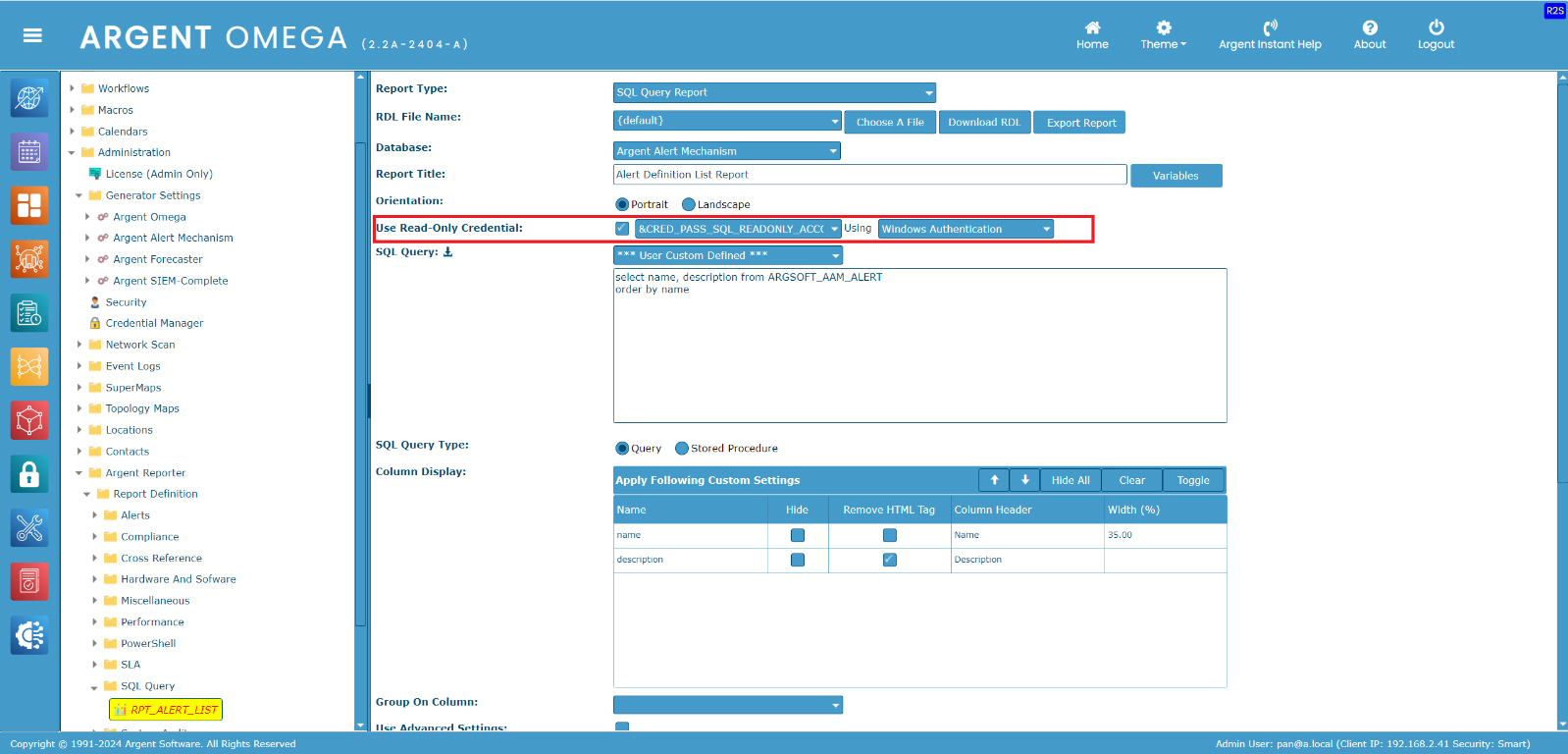
In cases that custom SQL query must be used, make sure to specify the read-only credential
There are two types of SQL logins – Windows Authentication and SQL Server Authentication
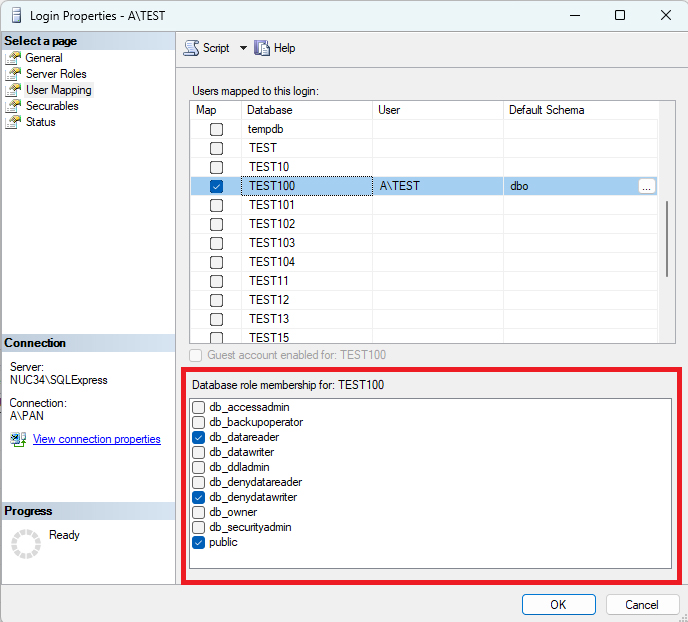
To make a SQL login READ-ONLY, specify Database Roles db_datareader, db_denydatawriter and public.
Then create User/Password Credential in Credential Manager
Use the defined credential in custom report. The report then won’t be able to delete or modify database.
Technical Background
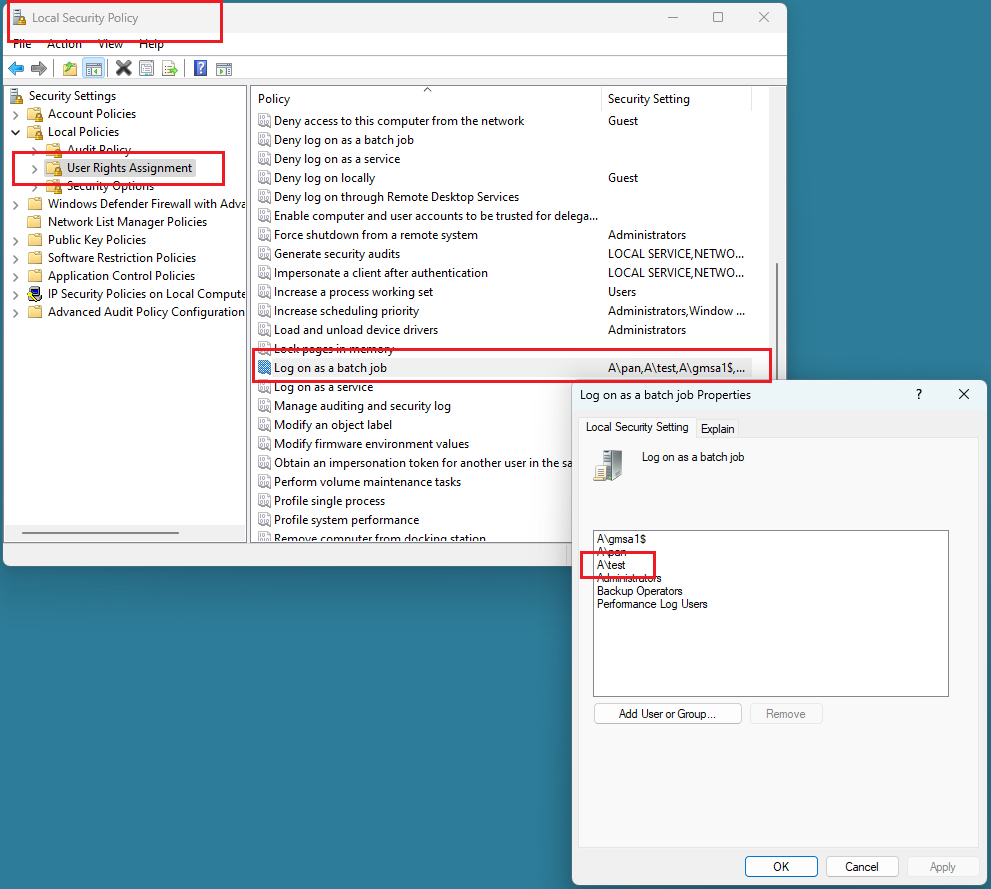
Argent Omega uses Impersonation to switch security context when the read-only account is a Windows account.
To do impersonation, the account must have user right of ‘Log on as a batch job’ on Argent Omega Generator machine
This is not necessary if a SQL Server account is used for authentication
Resolution
Upgrade to Argent Omega 2.2A-2404-A or later