KBI 312042 Filtering Windows Event Log using XPath In Windows Event Log Rules
Version
Argent Omega 2.2A-2301-A and above
Date
Thursday, 2 March 2023
Summary
Customers can use Windows Event Log Rules in Argent Compliance Automator to select and filter on specific Windows Event Log criteria for monitoring, archiving, or both. The Rule allows collecting and processing only the necessary event logs by configuring the appropriate filters. There are many filtering options available, such as filtering by a specific event source, event user, event category, filtering using XPath, filtering using UserData Variables, etc.
This document describes the usage XPath filtering option.
What Is XPath
Before we dive into XPath usage in Windows Event Log Rules, we need to understand what XPath is.
XPath is a method for selecting specific XML nodes from an XML document.
XPath stands for XML Path Language.
XPath uses “path like” syntax to identify and navigate nodes in an XML document.
How To View Windows Event In XML
Since Windows NT6 (Vista / Server 2008), events are saved in XML format.
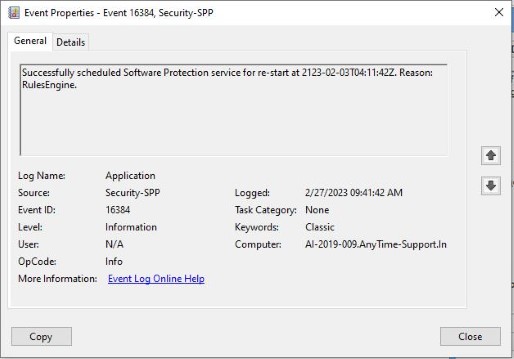
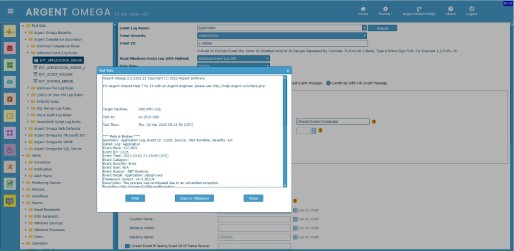
If we’ll take a look in event 16384:
The general message (Successfully scheduled Software Protection service for re-start at {0}.
Reason: {1}.) is saved in an external resource file, but the specifics (the replacement strings) are saved in the event.
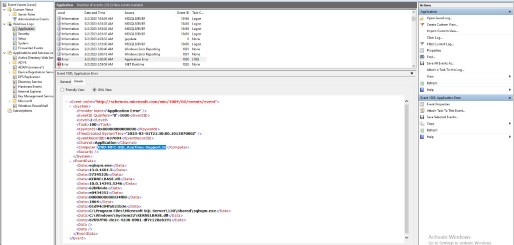
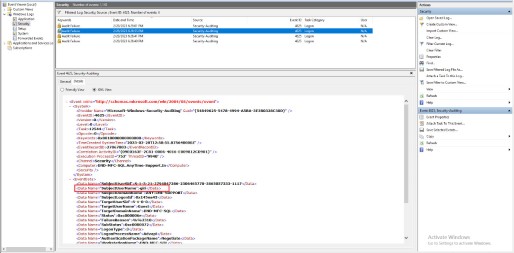
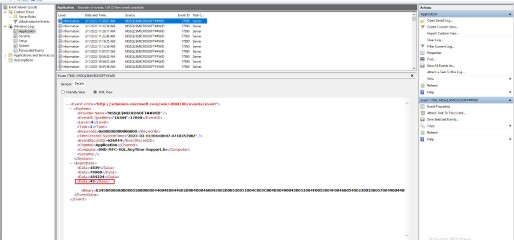
They can be viewed in a friendly view (Details/Friendly) or in their raw XML form (Details/XML):
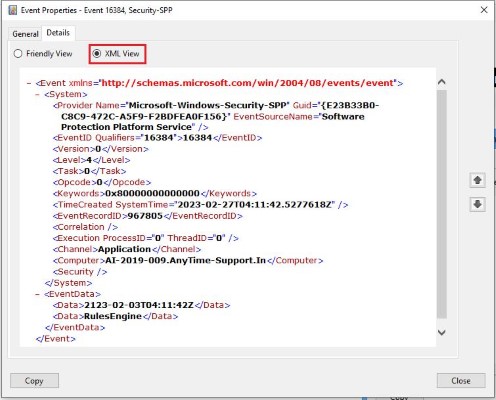
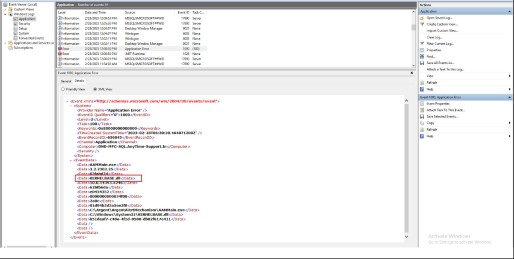
XML View:
See the event details, such as EventID, computer name, time created, etc., under the “System” node. It is possible to filter events using XPath on the event’s XML node.
XPath Syntax To Get Any Text Value Or Attribute Of XML
XPath uses path expressions to select nodes or node-sets in an XML document. For example, we will use the following event XML to describe path expressions:
The below table listed some XPath expressions of above XML and its results:
| XPath Expression | Result |
|---|---|
| / | The root node |
| /Event | Root element named “Event” |
| /Event/System | “System” element that is child of “Event” |
| /Event/System/Computer | Attribute named “Computer” that is a child of “System” that is a child of “Event” |
| /Event/EventData | “EventData” element that is child of “Event” |
| /Event/EventData/Data | First “Data” element that is the child of the “EventData”, that is a child of “Event” |
| /Event/EventData/Data[1] | First “Data” element that is the child of the “EventData”, that is a child of “Event” |
| /Event/EventData/Data[4] | Forth “Data” element that is the child of the “EventData”, that is a child of “Event” |
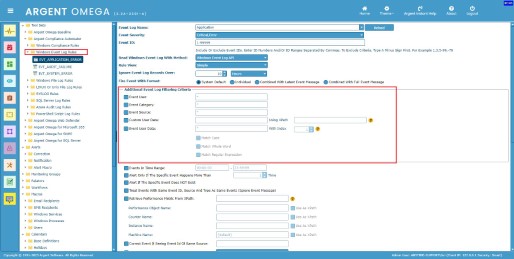
The Usage Of XPath In Windows Event Log Rules
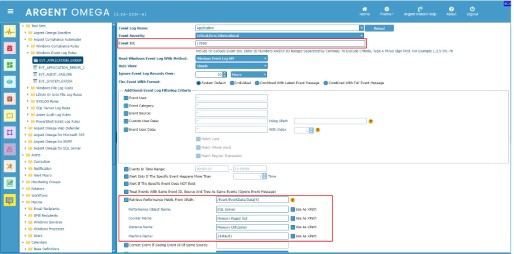
You can use XPath to filter event logs in Windows Event Log Rules.
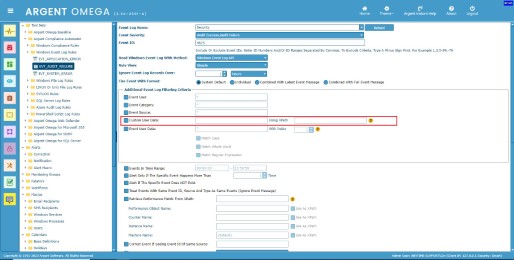
Specify the path expression in “Using XPath” input box.
Specify the matching attribute value in “Custom User Data” input box:
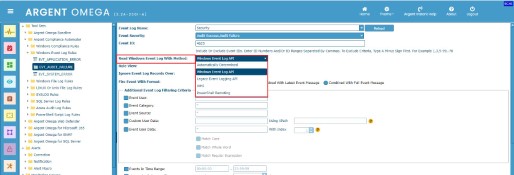
Use any of the following event log reading methods when using XPaths in Windows Event Log Rules:
- Windows Event Log API
- PowerShell Remoting
- Automatically Determined
Note:
The filtering options for Event ID and Event Time are already defined in the Rule. So there is no need to include these fields in an XPath expression.
Examples
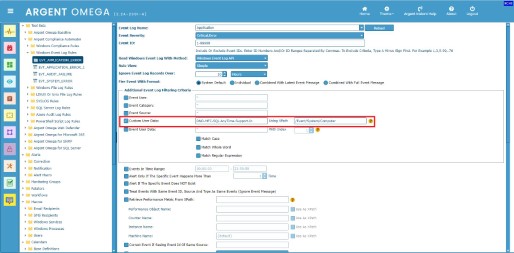
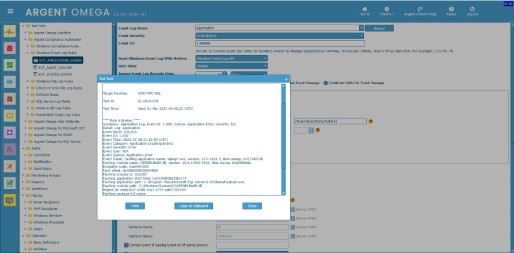
Example 1: Filter application error events that include a “Computer” name of “DND-MFC-SQL.AnyTime-Support.In” and that have occurred in the past 10 hours.
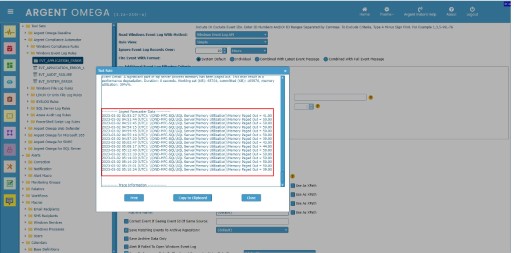
XML view of Application event log:
Rule Configuration:
Execution Result:
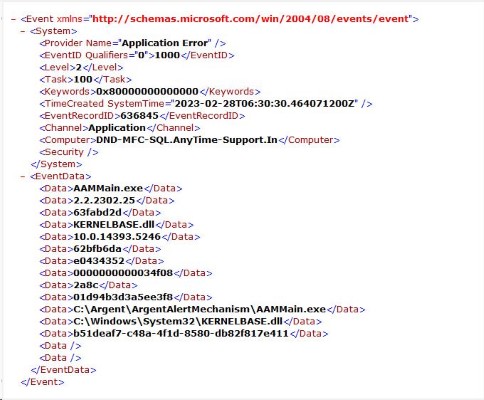
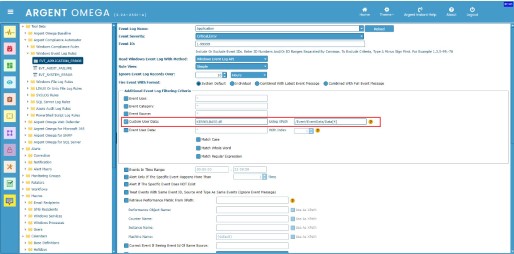
Example 2: Filter application error event logs with faulting module name “KERNELBASE.dll,” that have occurred in the past 10 hours:
XML view of Application event log:
Rule Configuration:
See the faulting module name is forth “Data” element, so the XPath expression is “/Event/EventData/Data[4]”
Execution Result:
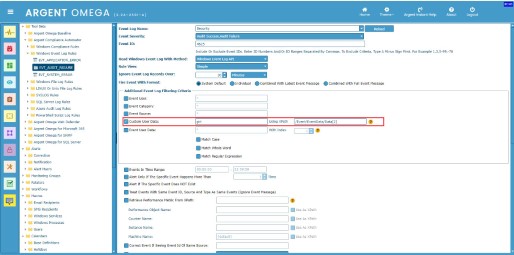
Example 3: Filter Security logon failure events for specific user.
XML view of Security event log:
Rule Configuration:
See the user name is in second “Data” element, so the XPath expression is “/Event/EventData/Data[2]”
Execution Result:
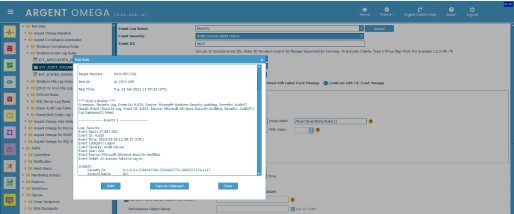
Example 4: Use XPath to retrieve Performance Metric in Windows Event Log Rule
XML view of event log:
Rule Configuration:
This event with ID 17,890 occurred because the memory committed to Microsoft SQL Server is paged out.
The Rule is configured to retrieve the memory utilization that is the fourth “Data” element in “EventData” section in XML.
Execution Result:
Technical Background
N/A
Resolution
Upgrade to Argent Omega 2.2A-2301-A or above