KBI 312043 Filtering Windows Event Log Using Advanced Filter String In Windows Event Log Rules
Version
Argent Omega 2.2A-2301-A and above
Date
Tuesday, 28 February 2023
Summary
Introduction:
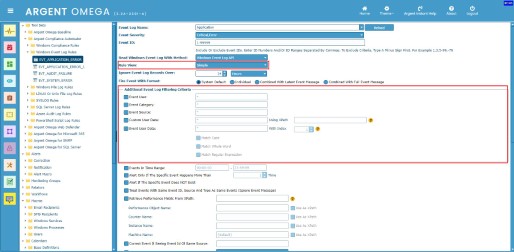
Customers can use Argent Compliance Automator’s Windows Event Log Rules to select and filter specific Windows Event Log criteria for monitoring, archiving, or both. The Rule allows for collecting and processing only the necessary event logs by configuring the appropriate filters. There are numerous filtering options available in the Windows Event Log Rule, which are divided into two categories: Simple and Advanced. The Simple mode allows filtering of event logs by a specific event source, event user, event category, filtering using XPath, filtering using UserData Variables, etc.
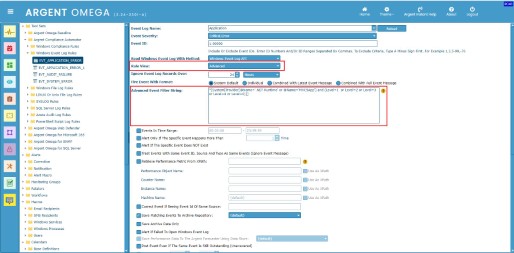
In Advanced mode, you need to specify an XPath query in Advanced Event Filter String field that identifies the events that you want to filter out.
The Windows event log stores logs and their metadata as XML documents. The XPath is a method for selecting specific XML nodes from an XML document. The XPath query gives you the ability to filter using a much wider range of criteria. Basically, you can search using anything that is presented in the list of XML values.
Use any of the following event log reading methods when using XPaths in Windows Event Log Rules:
- Windows Event Log API
- PowerShell Remoting
- Automatically Determined
Understanding XPath Query
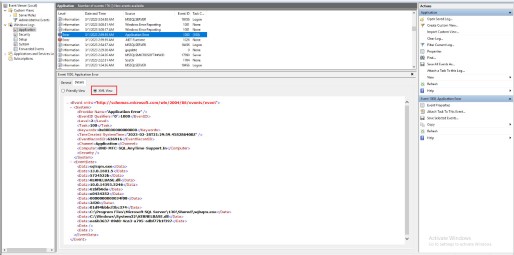
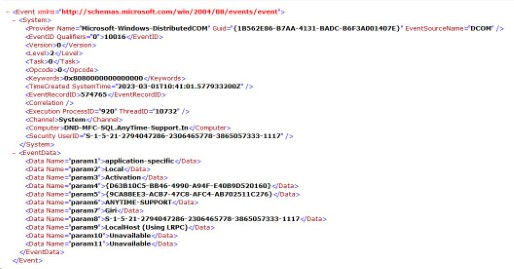
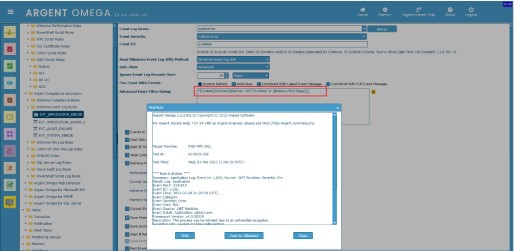
XPath is a method for selecting specific XML nodes from an XML document. XPath stands for XML Path Language. Since Windows NT6 (Vista / Server 2008), events are saved in XML format. For example, following is a XML view of a Windows event log record:
XPath query filters events on the event record’s XML node.
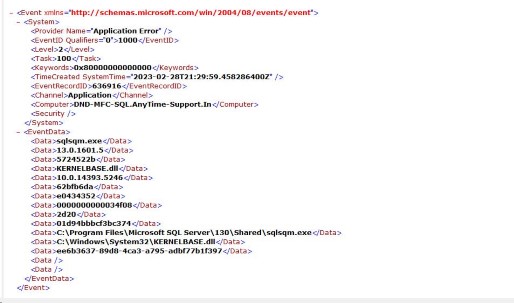
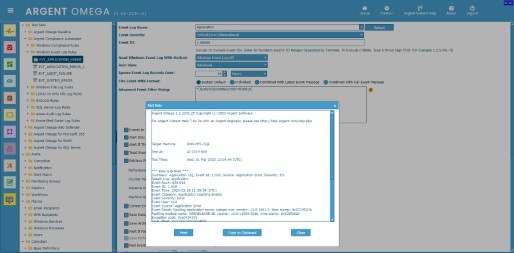
Take event XML of event ID 1,000 as an example:
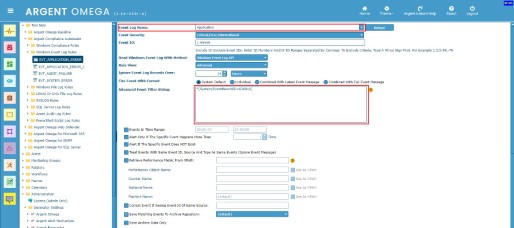
You can see in the XML that “Computer” element comes under “System” node. So the XPath query to fetch all the events with “Computer” name “DND-MFC-SQL.AnyTime-Support.In” is:
*[System/Computer=“DND-MFC-SQL.AnyTime-Support.In”]
XPath query to retrieve all the events with EventRecordID as 636,916 is:
*[System/EventRecordID=636916]
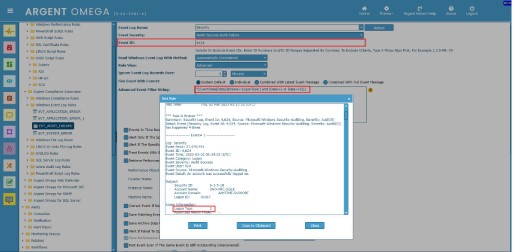
Specify the XPath query in Advanced Event Filter String field and test the Rule. The Rule will use the path specified in Event Log Name field to retrieve the events:
Note:
The filtering options for Event ID and Event Time are already defined in the Rule. So there is no need to include these fields in an XPath query.
Rule Test Result:
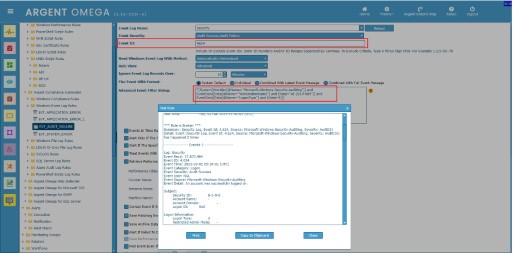
It is possible to filter event records based on element’s attribute value.
Consider the following event:
The following XPath query retrieves event entries with provider name is
“Microsoft-Windows-DistributedCOM”.
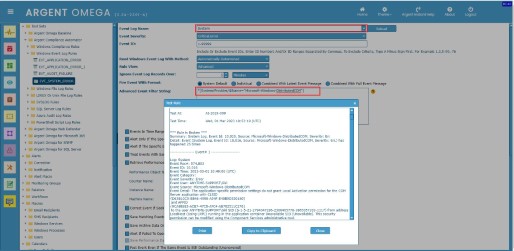
*[System/Provider/@Name=”Microsoft-Windows-DistributedCOM”]
Following is the Rule execution Result:
Following is a sample XPath query apply filter to elements in “EventData” node. The query retrieves all logon event records of “Interactive” and “Remote Interactive” users:
*[EventData[Data[@Name=’LogonType’] and (Data=2 or Data=10)]]
(‘LogonType’ is “2” for “Interactive” users and “10” for “Remote Interactive” users)
XPath query to retrieve all the critical and error events reported by ASP.NET application named “MVC5App”:
*[System[Provider[@Name=’.NET Runtime’ or @Name=’MVC5App’]]]
XPath query to retrieve all logon events that include a WorkstationName of “AI-2019-009” and a logon type of “3” (network):
*[System[Provider[@Name=”Microsoft-Windows-Security-Auditing”]] and
EventData[Data[@Name=”WorkstationName”] and (Data=”AI-2019-009″)] and
EventData[Data[@Name=”LogonType”] and (Data=3)]]
Technical Background
N/A
Resolution
Upgrade to Argent Omega 2.2A-2301-A or above