KBI 312063 Monitoring Active Directory And Domain Controllers Without Domain Admin Account
Version
Argent Omega and Argent Advanced Technology all versions
Date
Monday, 7 August 2023
Summary
It is typical to install Argent Omega or Argent AT with a service account that is a member of Domain Admins because Domain Admins is a member of the local group of Administrators. Being a local administrator, access to Performance Counters, Service Control Manager, Event Logs etc. are allowed by default.
This easy configuration might not meet customer’s stricter security requirements, especially when the monitored target machine is a Domain Controller. Also Domain Controllers do not have a local group ‘Administrators’. There is no way to directly add service account to local group ‘Adminstrators’ as it could be done for member servers.
With a little careful configuration, it can be done to monitor Active Directory and Domain Controllers without Domain Admin account.
Technical Background
Argent for Active Directory includes many useful pre-defined Rules to monitor Active Directory and Domain Controllers. Each Rule and its required configuration are explained below:
Performance Rules
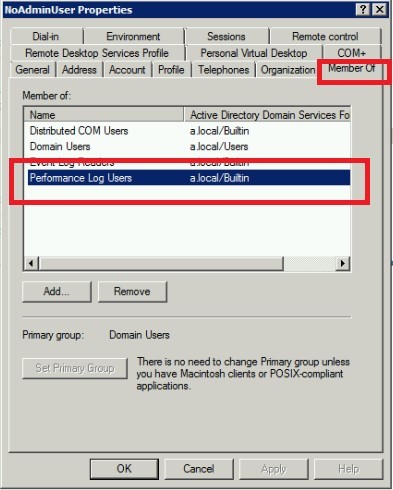
Add service account to local built-in group ‘Performance Log User’ at Domain Controller.
Note: In the past, there was another built-in group ‘Performance Monitor User’ in Windows 2012 and earlier. This group has not been created by default since Windows 2016— use the group ‘Performance Log User’ instead.
The show properties of service account in Active Directory Users and Computers.
Select tab ‘Member Of’, add group ‘Performance Log Users’, then click on Apply button.
Connectivity Rules
Connectivity Rules test specific TCP ports for different Domain Controller components.
It does not require any particular security configuration on the Domain Controller.
Service Rules
Windows machines do not allow remote access of Service Control Manager (SCM) for non-local-administrator account by default.
Argent includes utility ‘ARGSOFT_GRANT_SCM_ACCESS’ to grant read access to non-domain admin account. This utility has to be executed ONCE locally at each monitored Domain Controller.
Take following steps to accomplish this:
- Log on to Domain Controller as an Administrator.
- Copy ARGSOFT_GRANT_SCM_ACCESS.exe to a temp folder at Domain Controller.
- Run ‘ARGSOFT_GRANT_SCM_ACCESS service_account’ to allow read access to SCM.
- Run ‘ARGSOFT_GRANT_SCM_ACCESS service account service_name’ to allow read access to a specific service. Use ‘*’ for service_name to allow read access to ALL installed services.
After having executed step 3 and step 4, selected services on Domain Controller can be monitored remotely without Domain Admin.
DNS Rules
DNS Rules try to resolve specified DNS names. It does not require any particular security configuration on the Domain Controller.
Active Directory Rules
Active Directory Rules try to authenticate the specified user and password. It does not require any particular security configuration on the Domain Controller.
LDAP Query Rules
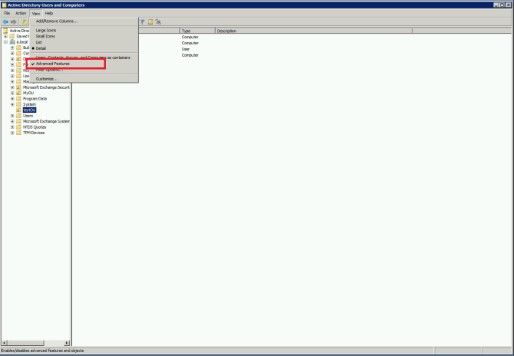
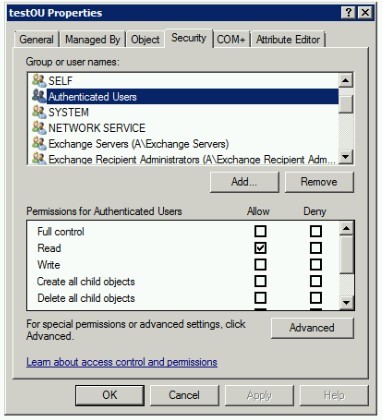
Activity Directory allows read access to LDAP objects by non-domain admin accounts by default. Each LDAP object has its own or inherited security configuration. If a particular LDAP object gives access deny error, check its security configuration in Active Directory Users and Computers.
Note: Advanced Features in menu ‘View’ must be enabled in order to see Security tab.
Event Log Rules
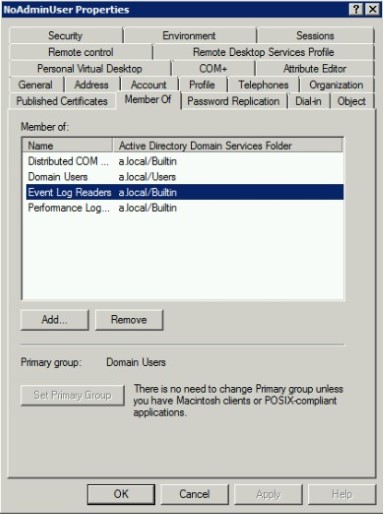
Add service account to local built-in group ‘Event Log Readers’ at Domain Controller.
Show properties of service account in Active Directory Users and Computers. Select tab ‘Member Of’, add group ‘Event Log Readers’, then click on Apply button.
PowerShell Script Rules
Sometimes it is required to run a PowerShell cmdlet on the Domain Controller. The PowerShell Remoting should be used in this case. Typically, PowerShell Remoting is only allowed for local administrators. To allow a non-domain admin account to do this, use following steps:
- Logon Domain Controller as Administrator.
- Run PowerShell as Administrator.
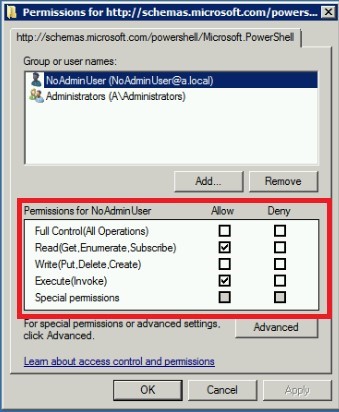
- Run command ‘Set-PSSessionConfiguration -Name Microsoft.PowerShell -ShowSecurityDescriptorUI -Force’
- Add service account and give Read and Execute permissions. Click button ‘Apply’.
Note: To enable PowerShell Remoting in general, refer to Argent KBI 311178 Enabling PowerShell Remoting.
The Set-PSSessionConfiguration command needs be run only once.
WMI Script Rules
WMI is reserved for local administrators by default. It is an older technology and requires more complicated configuration to allow non-domain admin account to monitor Domain Controllers.
To accomplish this, use following steps:
- Logon Domain Controller as Administrator.
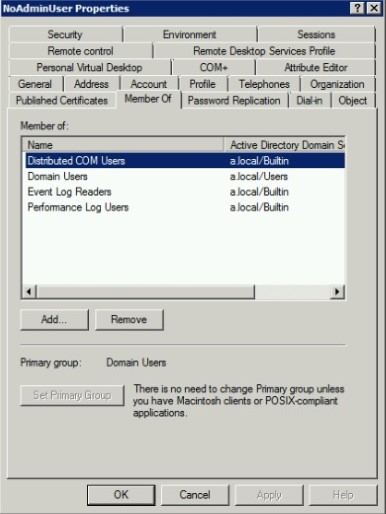
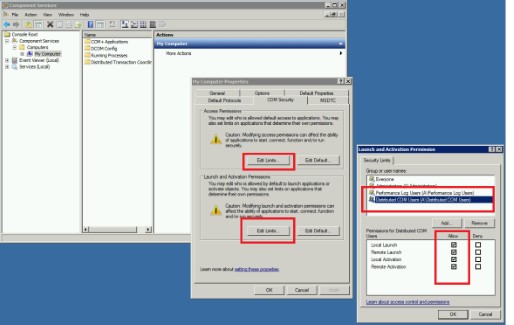
- Open ‘Active Directory Users and Computers’. Add service account to local group ‘Distributed COM Users’
- Run ‘dcomcnfg’. Verify groups ‘Distributed COM Users’ and ‘Performance Log Users’ have all the rights.
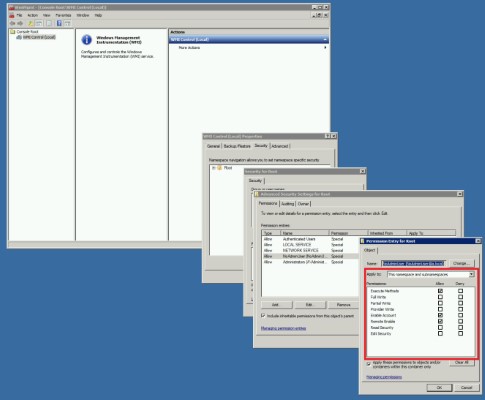
- Run ‘wmimgmt.msc’. Right-click WMI Control (Local) to bring up the menu and click ‘Properties’.
- Click the Security tab, then click ‘Root’, and click the ‘Security’ button.
- Add service account, then click ‘Advanced’.
- From the ‘Applies to’ drop-down list, select ‘This namespace and subnamespaces’
- Select Permissions at least ‘Execute Method’, ‘Enable Account’ and ‘Remote Enable’.
- Apply the changes.
Note: Customer does not have to enable all the permissions listed above. He can enable configuration selectively based the Rules he would like to run. For example, if the WMI Rule is not used, its corresponding security configuration can be safely skipped.
Resolution
For assistance please contact Argent Instant Help at https://Instanthelp.Argent.com/