KBI 311745 Issue Addressed: Failed To Connect To LINUX/Unix Server Using SSH After Hardening Linux Server
Version
Argent Advanced Technology 5.1A-1901-C and below
Date
Tuesday, 9 April 2019
Summary
Based on recommendation from Linux hardening best practices, SHA1 and MD5 Message Authentication Code (MAC) algorithms and cipher block chaining (CBC) encryption algorithms are considered unsafe or weak, such as hmac-sha1, hmac-sha1-96, hmac-md5, hmac-md5-96 and aes256-cbc, aes192-cbc, aes128-cbc and 3des-cbc
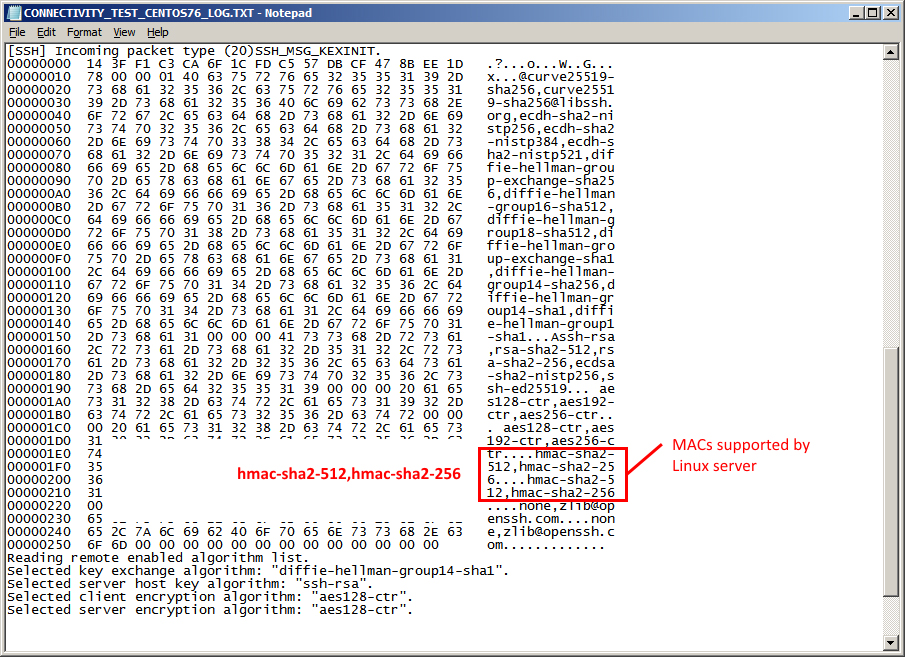
The currently considered safe or strong MACs are hmac-sha2-512, hmac-sha2-256, hmac-sha2-512-etm@openssh.com, hmac-sha2-256-etm@openssh.com, umac-128-etm@openssh.com, umac-128@openssh.com and aes256-ctr, aes192-ctr, aes128-ctr
Linux server hardening would require only specifying the strongest encryption algorithms in the configuration files on the SSH Daemon or Server
A SSH Daemon / Server configuration (/etc/ssh/sshd_config) with the following would be considered hardened
Ciphers aes128-ctr,aes192-ctr,aes256-ctr
MACs hmac-sha2-512,hmac-sha2-256
Technical Background
Argent AT Engine uses built-in SSH library by default to communicate with LINUX/Unix server
Argent AT Engine has to negotiate with LINUX/Unix server to pick encryption cipher that supported by both sides
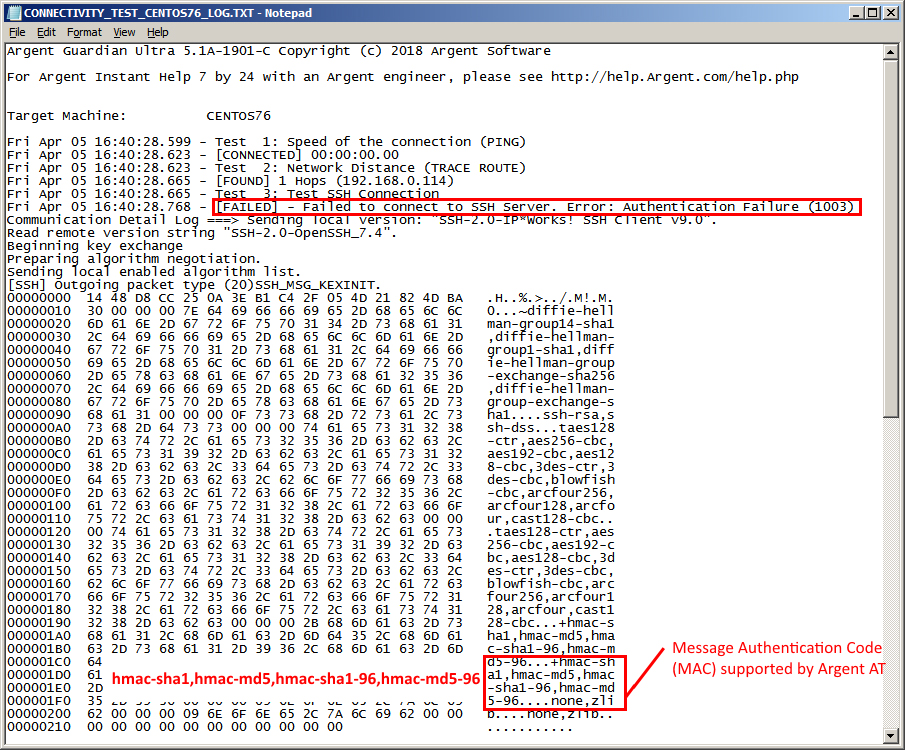
By default, Argent AT Engine sends out aes256-cbc, 3des-cbc, aes256-ctr as the supported encryption algorithms and hmac-sha1, hmac-md5, hmac-sha1-96, hmac-md5-96 as the supported MAC algorithms
As Argent AT Engine does not know what ciphers are disabled by Linux, both sides might end up with an encryption algorithm or MAC that is disabled by OS
As a result, the SSH connection fails
To see the detail, do connectivity testing in License Manager
Outgoing client supported MACs in Argent Advanced Technology 5.1-1901-C and below:
hmac-sha1, hmac-md5, hmac-sha1-96 and hmac-md5-96
If no client / server MAC combination is found, an error occurs
The SSH daemon server configuration file (sshd_conf) should have a matching MAC
Argent Advanced Technology 5.1A-1904-B is enhanced to allow customization of supported MAC algorithms
Registry HKLM\Software\ARGENT\COMMON\SSH_SUPPORTED_MAC_ALGORITHM can be used to specify the supported MAC algorithms
Multiple algorithms are separated by comma
For example, the registry string value can be “hmac-sha2-256, hmac-sha2-128” for communicating with hardened Linux servers
Note: User may have to use registry HKLM\Software\ARGENT\COMMON\SSH_SUPPORTED_ENCRYPTION_ALGORITHM too if cipher algorithm is also hardened
See KBI 311665 Issue Addressed: Failed To Connect To LINUX/Unix Server Using SSH After Hardening Windows Server for detail
Resolution
Upgrade to Argent Advanced TechnologyT 5.1A-1904-B or above
For customer who cannot upgrade immediately, he needs to rollback using PLINK instead of built-in SSH library
To do so, change registry value to 1 for registry
HKLM\Software\Argent\COMMON\SSH_LIBRARY