KBI 311918 How To Create Group Management Service Account gMSA
Version
All versions
Date
Wednesday, 24 Mar 2021
Summary
Group Managed Service Accounts provide:
– Automatic password and SPN management to multiple servers in a farm
– A single identity for services running on a farm
Managed Service Accounts are Active Directory accounts that are assigned to certain computers.
The passwords on these accounts are long and complex and are maintained automatically.
This means that the passwords are generated on their own every 30 days.
Having long, complex, and self-generated passwords makes the accounts more secure.
Group Managed Service Account (gMSA) was first introduced in Windows Server 2012 and takes the same functionality as Managed Service Accounts and extends its functionality into multiple servers.
Advantages Of gMSA
All the newly created gMSA accounts have minimal rights. Any additional rights must be explicitly defined.
Unlike locally stored standard service passwords, gMSA passwords are generated randomly and stored on the Active Directory domain controller and the password is complex and contains 120 characters.
And for the standard configuration, the password is automatically changed every month.
There is no need for anyone to enter, document or see a password for his/her gMSA account at any time. The computer that runs the service and the Active Directory domain controller do it automatically.
Requirements:
– Need to have at least one domain controller running Windows Server 2012 so it can store managed password information.
– The client computers that are going to use these accounts must be Windows 8 or newer
– Server-based computers must have Windows Server 2012 or newer
– Need to do before creating a gMSA is create a KDS root key on the domain controller in the domain
Technical Background
Create Group Managed Service Account
1. Create a hosting Domain Group, say ‘gmsa1Group’
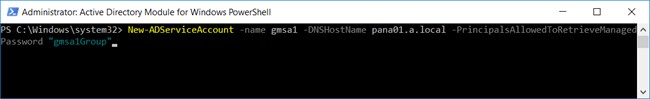
2. Create account ‘gmsa1’. Run PS Command
New-ADServiceAccount -name gmsa1 -DNSHostName pana01.a.local -PrincipalsAllowedToRetrieveManagedPassword “gmsa1Group”
Account name – gmsa1
Domain Controller – pana01.a.local
Hosting Group – gmsa1Group
Customize the command accordingly Associate Group Managed Service Account with Argent AT Engine
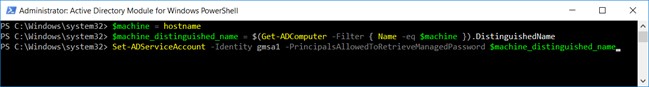
1. Allow Argent AT Engine to use the gMSA
$machine = hostname
$machine_distinguished_name = $(Get-ADComputer -Filter { Name -eq $machine }).DistinguishedName
Set-ADServiceAccount -Identity gmsa1 -PrincipalsAllowedToRetrieveManagedPassword $machine_distinguished_name
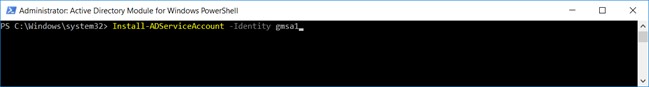
2. Install gMSA on Argent AT Engine
Install-ADServiceAccount -Identity gmsa1
3. Test gMSA is installed properly
Test-ADServiceAccount gmsa1
Add gMSA to Appropriate Domain Groups
Argent AT service account requires Administrator privilege on local machine to run as service, also needs sufficient Domain rights to do remote monitoring.
Typically, Argent AT service account is a member of Domain Admins.
It is found that gMSA simply does not show up when updating group members using Administrative Tools. It is easier to do using PowerShell.
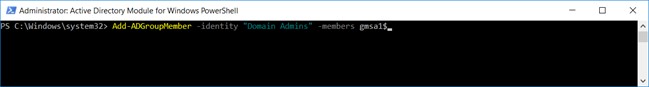
1. Add gMSA to Domain Admins
Add-ADGroupMember -identity “Domain Admins” -members gmsa1$
Note: Do NOT forget the trailing ‘$’ for gMSA
2. Test property ‘member of’.
Get-ADServiceAccount -Identity “gmsa1” -Properties Memberof
Resolution
N/A