How Does Argent Defender Secure Its Communication?
This article explains how the Argent Defender communicates with remote Argent Defender Trusted Agents.
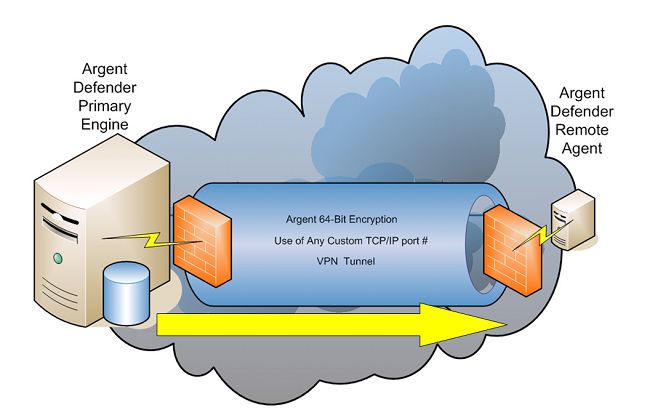
The Argent Defender Trusted Agent listens on port 3209 by default.
Sensitive information from each recorded transaction is securely stored within the Argent Defender’s local database. When a test is submitted to a Trusted Agent, the Argent Defender maintains the security of the web site transaction whether the Trusted Agent is on the local network or across the Internet.
The Argent Defender Main Engine initiates communication to the Argent Defender Trusted Agents and uses a built-in CRC (Cyclic Redundancy Check) within each packet to prevent any external data manipulation. Using this built-in encryption mechanism prevents external data peeking at a very low resource cost.
The 64-bit CRC is created for each request packet and reply packet. This prevents corrupted data from ever being transmitted. Though TCP guarantees the integrity of the packet, Argent Research has found occurrences of one in 10**9 packets being bad.
The Argent Defender changes the seed for encrypting request and reply packets. As the encryption seed is different for each packet, deciphering the packets is effectively impossible.
The timing for periodical connection to the Remote Defender Agent service is fully randomized within the specified period. This technique prevents remote agents from connecting to the central engine simultaneously and saturating the channel.
The Argent Defender Trusted Agent has been used across a variety of connections from LAN based to VPN connections. Many Customers use the Argent Defender Trusted Agents within VPN connections for added security.